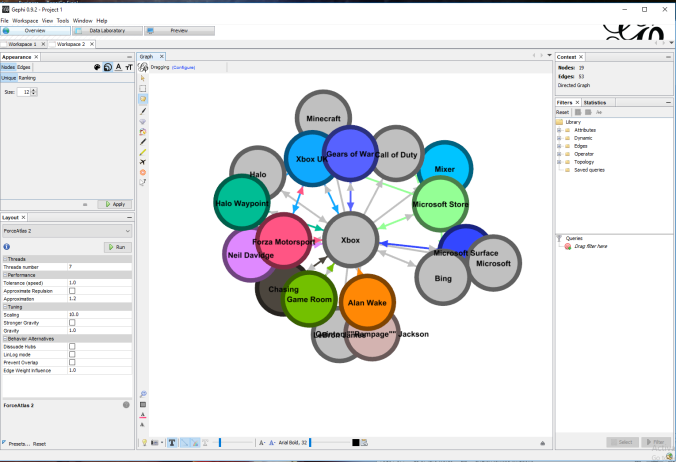
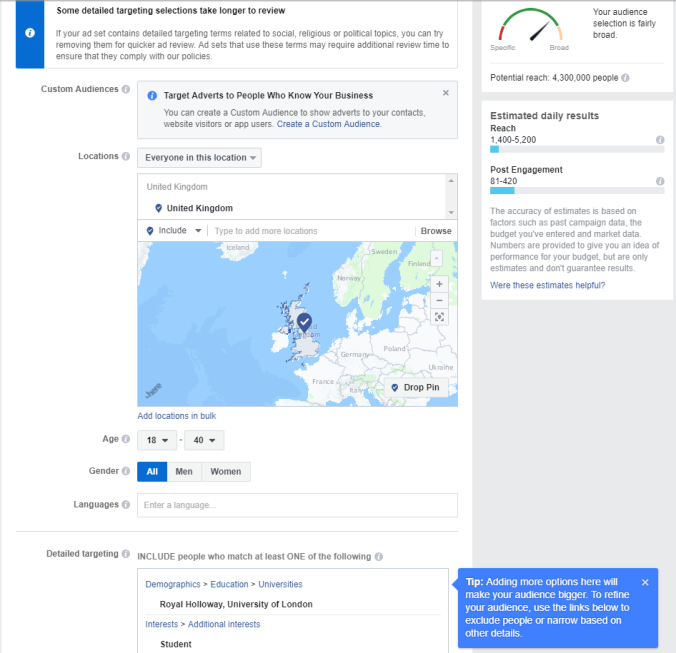
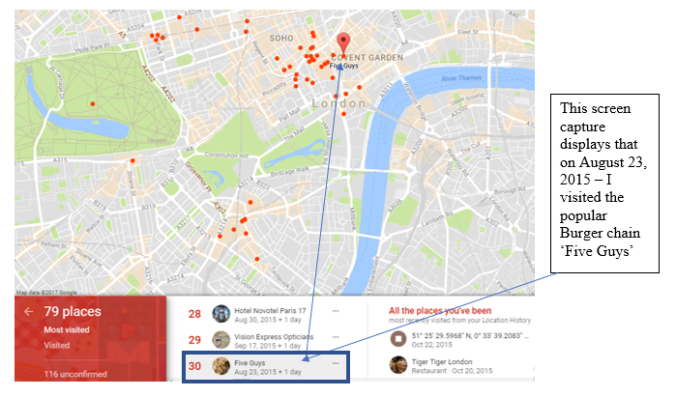
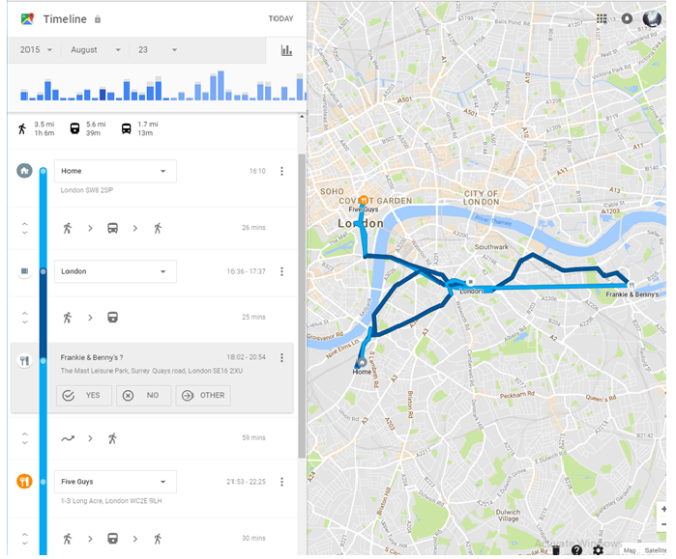
Over the course of this module I have discovered the technical intricacies of the online platform. The most surprising read was based on the datafication that some websites are able to manage due to the large abundance of data they receive from consumers using their websites. The Facebook Ads running online that specifically target users based on characteristics such as occupation, political view, living location and even if you have a child is surprising to me. It creates a sense of insecurity of data and therefore I feel obliged to tighten up my habits of updating personal information every so often other than LinkedIn as that is purely a professional networking website.
These teachings of social media metrics (consumption, engagement, lead-generation and sales) will undoubtedly help my research in my marketing major and career. It has been an insightful experience to discuss the investment within websites, the short term returns and the long term returns. This can be done through product awareness, building the brand image and reputation and gaining consumer loyalty. As the founder of Quaker once said, he would take all the trademarks and branding whilst leaving his partner the bricks and mortar of the physical shop and he would still fare better than his counterpart. The reason for this is the importance of social contagion and the effectiveness of the advertising they are able to utilise.
The social narratives, location, demographics, behaviours, connections, relevant events, timed events and trending topics are all things I will now consider when discussing the use of social networking/media in advertising. The social network is an incredibly powerful tool, as the modernisation of the industry has allowed us to track the statistics of effective advertisements, rather than static posters that can only be tracked through the recording of increased sales and servicing. This is especially true for tailored marketing – as Eric Schmidt once quoted “The power of individual targeting – the technology will be so good it will be very hard for people to watch or consume something that, has not in some sense been tailored for them’. This ties into the consequences of personalisation and another interesting topic that I learnt about is the cultural differences and requirements that different countries use in their social networking applications.
Japan use LINE, Korea use KAKAO, China use WeChat and the majority of Europe use WhatsApp and Facebook. The vast differences in application hold the same principle, however China’s WeChat is exclusive only to China, almost like a mass internal server that is cut off from outside sources. With it, the consumers are able to do a wide range of activities such as pay for their utility bills, order a taxi, sort banking errands, order food etc things to help them with their daily lives. Whereas WhatsApp and Facebook Messenger only hold the purpose of chatting and this is the difference in culture and regards of their online data for safety and protection.
Do the human rights laws and censorship laws in China make this type of mass abundance of data acceptable to them? Is there a reason why Europe is susceptible to adopt a similar style of wide use application based on the security threats?
It is these types of questions that MN3536 has prompted me to ask about many things in the course, it has sparked critical thinking and been an utmost enjoyable course.